Web Shell | b374k 3.2.3
b374k web shell has been around for a few years. Its author periodically releases a new version. The latest version that can be identified so far is 3.2.3.
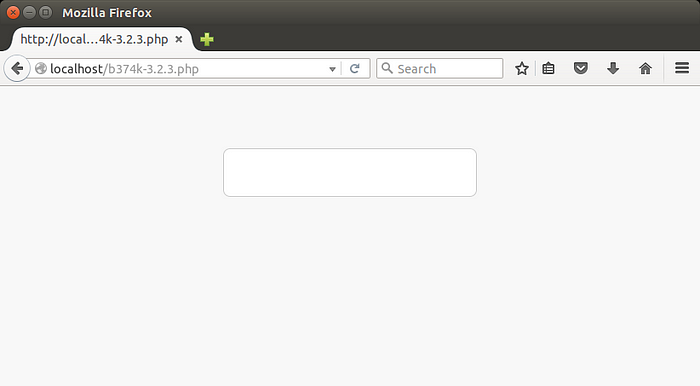
This version is like previous ones which require the password to load the main page. Once this shell is executed on the web server, it will display the input field, shown above, for the attackers to type the password.
The default password is “b374k” (without quotes). However it can be changed by the attackers.
Once the correct password is entered, the main page will be unlocked. The b374k author has developed a packer to allow attackers to create b374k shells with different themes. Therefore, the main page may have different colors and styles.
This shell appears to have the following functions.
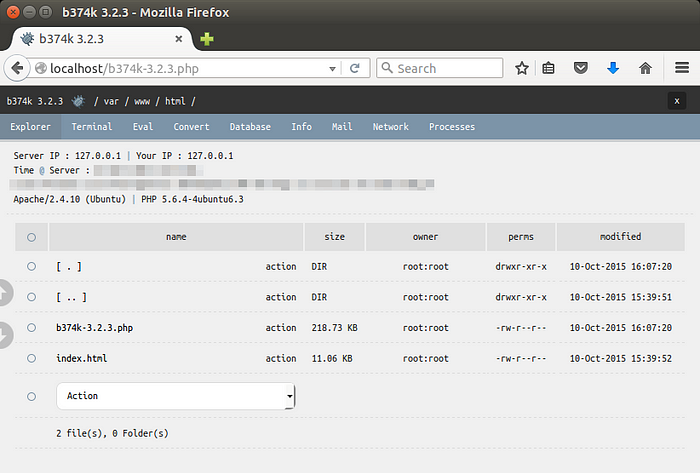
● File manager (view, edit, rename, delete, upload, download, archiver, etc)
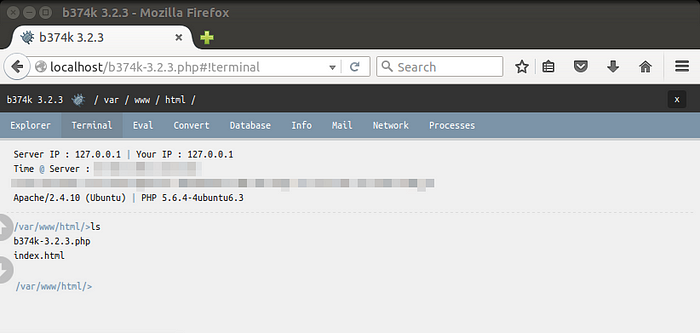
● Command execution
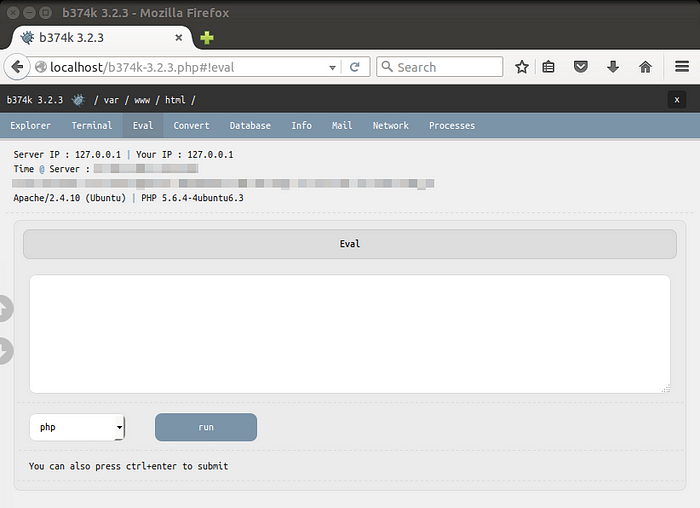
● Script execution (php, perl, python, ruby, java, node.js, c)
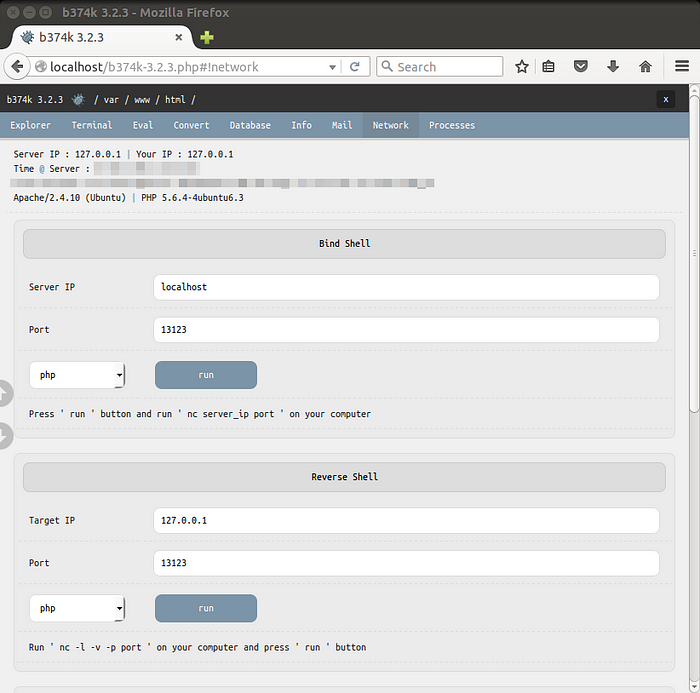
● Bind/reverse shell
● Simple packet crafter
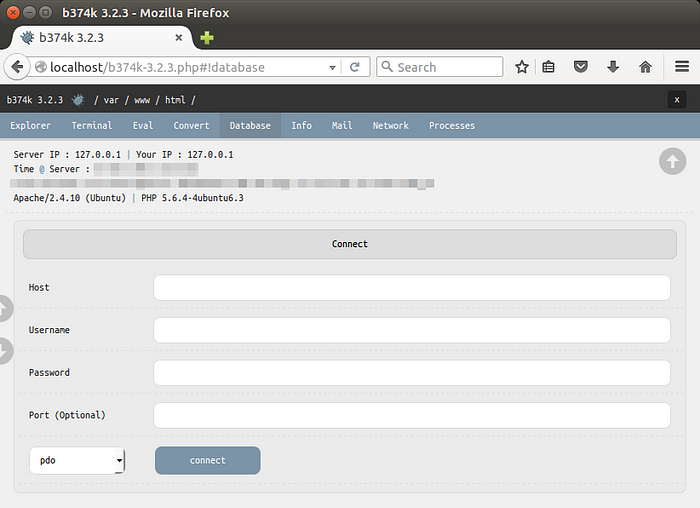
● Connect to DBMS (mysql, mssql, oracle, sqlite, postgresql, and many more using ODBC or PDO)
● SQL Explorer
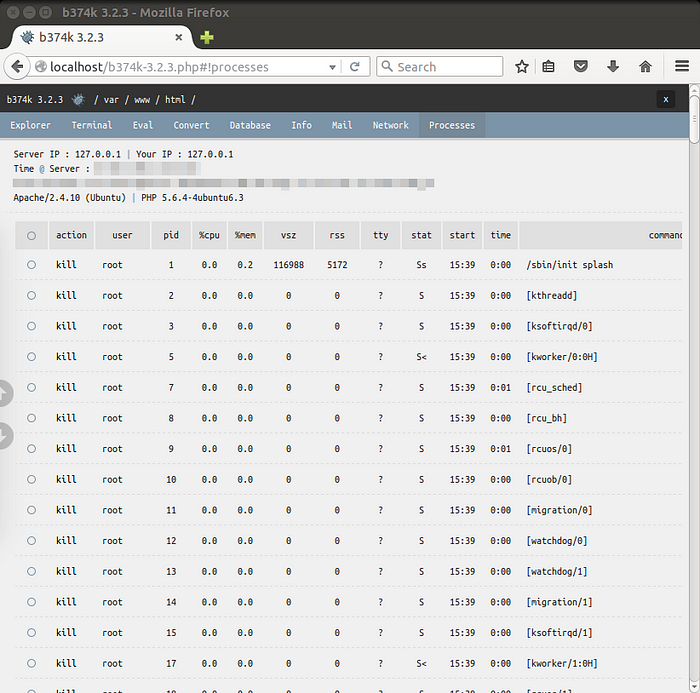
● Process list/Task manager
● Send mail with attachment (you can attach local file on server)

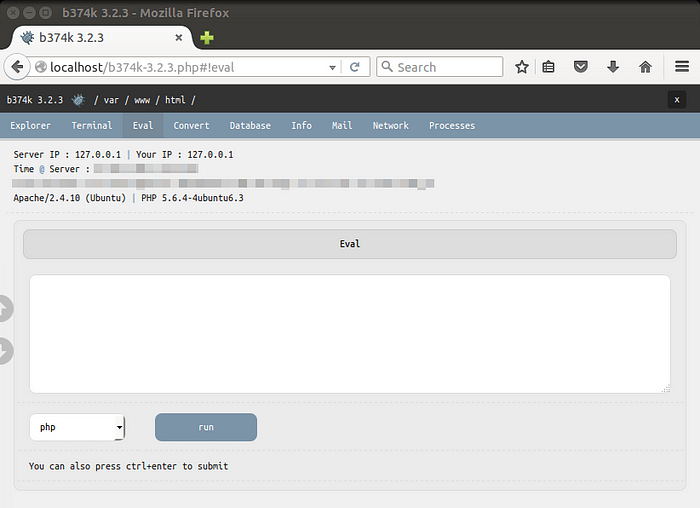
● String conversion
● Server information display
The b374k packer can produce this shell in various forms which may be able to avoid the detection and create difficulties for the code analysis. This packer will be introduced in the following blog.
Originally published at https://www.tumblr.com on October 10, 2015.
